1Y0-341 techniques - Citrix ADC Advanced Topics - Security Management and Optimization (CCP-AppDS) Updated: 2024

 |
 |
 |
 |
 |
 |
 |
 |
1Y0-341 Citrix ADC Advanced Topics - Security Management and Optimization (CCP-AppDS)
Exam Specification: 1Y0-341 Citrix ADC Advanced Topics - Security Management and Optimization
Exam Name: 1Y0-341 Citrix ADC Advanced Topics - Security Management and Optimization
Exam Code: 1Y0-341
Exam Duration: 2 hours
Passing Score: 65%
Exam Format: Multiple-choice
Exam Delivery: In-person proctored exam
Course Outline:
1. Introduction to Citrix ADC Security and Optimization
- Overview of Citrix ADC and its role in security and optimization
- Understanding the importance of security management and optimization
- Exploring advanced topics related to Citrix ADC security and optimization
2. Advanced Security Features and Configuration
- Configuring advanced security policies and features
- Implementing SSL/TLS offloading and client certificate authentication
- Protecting against common web attacks using Citrix ADC
3. Traffic Optimization and Load Balancing
- Advanced traffic optimization techniques
- Load balancing configurations and algorithms
- Implementing global server load balancing (GSLB) for high availability
4. Citrix ADC Management and Troubleshooting
- Managing Citrix ADC appliances and configurations
- Monitoring and troubleshooting security and optimization issues
- Utilizing logs and diagnostic tools for problem resolution
5. Citrix ADC Security Best Practices
- Implementing security best practices for Citrix ADC deployments
- Securing Citrix ADC management interfaces and access
- Auditing and compliance considerations for Citrix ADC security
Exam Objectives:
1. Understand the role and importance of security management and optimization in Citrix ADC.
2. Configure advanced security features and policies in Citrix ADC.
3. Implement SSL/TLS offloading and client certificate authentication.
4. Protect against common web attacks using Citrix ADC.
5. Optimize traffic and load balancing using Citrix ADC.
6. Implement global server load balancing (GSLB) for high availability.
7. Manage and troubleshoot Citrix ADC appliances and configurations.
8. Monitor and troubleshoot security and optimization issues.
9. Implement security best practices for Citrix ADC deployments.
10. Secure Citrix ADC management interfaces and access.
11. Understand auditing and compliance considerations for Citrix ADC security.
Exam Syllabus:
Section 1: Introduction to Citrix ADC Security and Optimization (10%)
- Overview of Citrix ADC and its role in security and optimization
- Importance of security management and optimization
- Advanced topics in Citrix ADC security and optimization
Section 2: Advanced Security Features and Configuration (30%)
- Configuring advanced security policies and features
- Implementing SSL/TLS offloading and client certificate authentication
- Protecting against common web attacks using Citrix ADC
Section 3: Traffic Optimization and Load Balancing (20%)
- Advanced traffic optimization techniques
- Load balancing configurations and algorithms
- Implementing global server load balancing (GSLB) for high availability
Section 4: Citrix ADC Management and Troubleshooting (25%)
- Managing Citrix ADC appliances and configurations
- Monitoring and troubleshooting security and optimization issues
- Utilizing logs and diagnostic tools for problem resolution
Section 5: Citrix ADC Security Best Practices (15%)
- Implementing security best practices for Citrix ADC deployments
- Securing Citrix ADC management interfaces and access
- Auditing and compliance considerations for Citrix ADC security
Citrix Optimization techniques
Other Citrix exams
1Y0-203 Citrix XenApp and XenDesktop 7.15 Administration1Y0-440 Architecting a Citrix Networking Solution (CCE-AppDS)
1Y0-204 Citrix Virtual Apps and Desktops 7 Administration
1Y0-403 Citrix Virtual Apps and Desktops 7 Assessment, Design and Advanced Configurations
1Y0-312 Citrix Virtual Apps and Desktops 7 Advanced Administration (CCP-V)
1Y0-341 Citrix ADC Advanced Topics - Security Management and Optimization (CCP-AppDS)
1Y0-241 Deploy and Manage Citrix ADC with Traffic Management
1Y0-231 Deploy and Manage Citrix ADC 13 with Citrix Gateway
1Y0-341
Citrix ADC Advanced Topics - Security? Management
and Optimization
https://killexams.com/pass4sure/exam-detail/1Y0-341
Question: 51
Scenario: A Citrix Engineer used Learning to establish the HTML SQL Injection relaxations for a critical web
application. The engineer now wishes to begin working on the protections for a different web application. The name of
the Web App Profile is appfw_prof_customercare.
Which CLI command can the engineer use to empty the Learn database?
A. set appfw learningsettings appfw_prof_customercare -SQLInjectionMinThreshold 0
B. set appfw learningsettings appfw_prof_customercare -startURLMinThreshold 0
C. reset appfw learningdata
D. export appfw learningdata appfw_prof_customercare
Answer: C
Question: 52
Scenario: A Citrix Engineer wants to configure the Citrix ADC for OAuth authentication. The engineer uploads the
required certificates, configure the actions, and creates all the necessary policies. After binding the authentication
policy to the application, the engineer is unable to authenticate.
What is the most likely cause of this failure?
A. The log files are full.
B. The Redirect URL is incorrect.
C. The certificates have expired.
D. The policy bindings were assigned incorrect priorities.
Answer: D
Explanation:
Reference: https://docs.citrix.com/en-us/citrix-adc/current-release/aaa-tm/entities-of-authentication-authorization-
auditing/authentication-policies.html
Question: 53
Scenario: A Citrix Engineer has enabled the IP Reputation feature. The engineer wants to protect a critical web
application from a distributed denial of service attack.
Which advanced expression can the engineer write for a Responder policy?
A. CLIEN
B. I
C. SR
D. IPREP_THREAT_CATEGORY(SPAM_SOURCES)
E. CLIEN
F. I
G. SR
H. IPREP_THREAT_CATEGORY(BOTNETS)
. CLIEN
. I
. SR
. IPREP_THREAT_CATEGORY(WEB_ATTACKS)
. CLIEN
. I
. SR
. IPREP_THREAT_CATEGORY(WINDOWS_EXPLOITS)
Answer: C
Question: 54
A Citrix Engineer needs to set up access to an internal application for external partners.
Which two entities must the engineer configure on the Citrix ADC to support this? (Choose two.)
A. SAML Policy
B. SAML IdP Profile
C. SAML IdP Policy
D. SAML Action
Answer: A,C
Explanation:
Reference: https://www.citrix.com/blogs/2015/04/09/how-to-use-saml-authentication-with-storefront-2-6/
Question: 55
Which report can a Citrix Engineer review to ensure that the Citrix ADC meets all PCI-DSS requirements.
A. Generate Application Firewall Configuration
B. PCI-DSS Standards
C. Application Firewall Violations Summary
D. Generate PCI-DSS
Answer: D
Explanation:
Reference: https://docs.citrix.com/en-us/citrix-adc/current-release/application-firewall/stats-and-reports.html
Question: 56
Scenario: A Citrix Engineer is monitoring the environment with Citrix Application Delivery Management (ADM).
Management has asked for a report of high-risk traffic to protected internal websites.
Which dashboard can the engineer use to generate the requested report?
A. App Security
B. Transactions
C. Users & Endpoints
D. App
Answer: B
Question: 57
A Citrix Engineer wants to delegate management of Citrix Application Delivery Management (ADM) to a junior team
member.
Which assigned role will limit the team member to view all application-related data?
A. readonly
B. appReadonly
C. admin
D. appAdmin
Answer: B
Explanation:
Reference: https://docs.citrix.com/en-us/citrix-application-delivery-management-service/setting-up/configuring-role-
based-access-control.html
Question: 58
A Citrix Engineer is reviewing the log files for a sensitive web application and notices that someone accessed the
application using the engineer’s credentials while the engineer was out of the office for an extended period of time.
Which production can the engineer implement to protect against this vulnerability?
A. Deny URL
B. Buffer Overflow
C. Form Field Consistency
D. Cookie Consistency
Answer: C
Question: 59
Which data populates the Events Dashboard?
A. Syslog messages
B. SNMP trap messages
C. API calls
D. AppFlow IPFIX records
Answer: D
Question: 60
Scenario: A Citrix Engineer configured signature protections for Citrix Web App Firewall. Signature Auto-Update has
been enabled. Upon reviewing the log files, the engineer notices that the auto update process has an error. In the
settings for Signature Auto Update the engineer notices that the URL is blank.
Which URL should the engineer enter to restore the update process?
A. https://s3.amazonaws.com/NSAppFwSignatures/SignaturesMapping.xml
B. https://download.citrix.com/NSAppFwSignatures/SignaturesMapping.xml
C. https://www.citrix.com/NSAppFwSignatures/SignaturesMapping.xml
D. https://citrix.azure.com/NSAppFwSignatures/SignaturesMapping.xml
Answer: A
Explanation:
Reference: https://support.citrix.com/article/CTX138858
For More exams visit https://killexams.com/vendors-exam-list
Crossref Citations
This Book has been cited by the following publications. This list is generated based on data provided by Crossref.
De Marchi, Alberto Jia, Xiaoxi Kanzow, Christian and Mehlitz, Patrick 2023. Constrained composite optimization and augmented Lagrangian methods. Mathematical Programming, Vol. 201, Issue. 1-2, p. 863.
Sushchenko, Olha Bezkorovainyi, Yurii Ostroumov, Ivan Zaliskyi, Maksym Averyanova, Yuliya and Larin, Vitalii 2023. Identification of Disturbed Stabilization Systems based on Experimental Data. p. 1.
Wang, Xiaoyu and Benning, Martin 2023. A lifted Bregman formulation for the inversion of deep neural networks. Frontiers in Applied Mathematics and Statistics, Vol. 9, Issue. ,
Borkar, Vivek S. and Rao, K. S. Mallikarjuna 2023. Elementary Convexity with Optimization. Vol. 83, Issue. , p. 131.
Sushchenko, Olha and Salyuk, Oleksandr 2023. Proceedings of the International Workshop on Advances in Civil Aviation Systems Development. Vol. 736, Issue. , p. 73.
Grippo, Luigi and Sciandrone, Marco 2023. Introduction to Methods for Nonlinear Optimization. Vol. 152, Issue. , p. 229.
The vulnerability’s name has been popping up over the past couple months in reports on key sectors. According to a post from cybersecurity researcher Kevin Beaumont, this flaw may be behind the cyber attack that disrupted swathes of credit unions earlier this week. The credit unions’ technology vendor Ongoing Operations was hit with ransomware and had failed to patch the vulnerability, he wrote. Ongoing Operations declined to confirm to Government Technology whether Citrix Bleed had been exploited.
But the health-care sector is also raising warnings. Industry group the American Hospital Association urged its membership recently to patch and defend against the vulnerability. Its message amplified the federal Health Sector Cybersecurity Coordinating Center (HC3)’s own alert. Ransomware actors also exploited it in an attack on airplane giant Boeing.
The flaw, also known as CVE 2023-4966, impacts Citrix NetScaler web application delivery control and NetScaler Gateway appliances. Federal officials and partners turned a spotlight on the vulnerability and issued a joint advisory, giving advice and details, including indicators of compromise; observed tactics, techniques and procedures; and detection methods.
Advisory authors include the Cybersecurity and Infrastructure Security Agency, FBI, Multi-State Information Sharing and Analysis Center and Australia’s lead cybersecurity agency, the Australian Signals Directorate’s Australian Cyber Security Centre.
At least one group of threat actors has been identified exploiting Citrix Bleed: affiliates deploying LockBit 3.0 ransomware. LockBit affiliates have in the past targeted organizations in critical infrastructure sectors, including government and emergency services, health care, financial services, energy, education, food and agriculture, manufacturing and transportation, per the joint advisory.
Hackers exploiting Citrix Bleed can “bypass password requirements and multifactor authentication leading to successful session hijacking of legitimate user sessions on Citrix NetScaler web application delivery control and Gateway appliances,” the advisory says. “Through the takeover of legitimate user sessions, malicious actors acquire elevated permissions to harvest credentials, move laterally, and access data and resources.”
The flaw is also relatively easy to exploit and so is likely to be widely exploited “in unpatched software services throughout both private and public networks,” per the advisory.
To respond, organizations should adopt updates, as well as search for evidence of compromise (and then take appropriate responses) as well as adopt other mitigation steps outlined in the joint advisory.
Citrix released the patch in early October, but attackers are known to have been exploiting it since August 2023.
“The manufacturer has also warned that these compromised sessions will still be active after a patch has been implemented,” HC3 wrote.
As such, HC3 advised not only updating but also using certain commands to remove “any active or persistent sessions.” The commands are below:
• kill aaa session -all
• kill icaconnection -all
• kill rdp connection -all
• kill pcoipConnection -all
• clear lb persistentSessions
SSD or Solid State Drive is a great way to increase your read and write pace by leaps and bounds. But there is still a lot you can do to improve the performance further. This article will give you some SSD optimization tips for better performance, so, go through them and pick the one that you like.

Following are the SSD optimization tips for better performance on your Windows 11/10 computer:
- Make sure to get the right device
- Disable Fast Startup
- Turn on TRIM
- Update SSD Firmware and Driver
- Enable AHCI
- Optimize SSD using Crucial Storage Executive
- Manage Write Caching
- Use High-Performance Power Plan
Let us talk about them in detail.
1] Make sure to get the right device
You can not just get a random SSD and call it a day. Every device has some specification and you need to make sure that you are getting the right one. If you are on a desktop computer and are planning to get a SATA SSD, the first thing worth checking is the availability of slots or cables to plug the device in. Lack of space can force you to bug a Y-split cable, which is not a bad option, to plug in the drive. Apart from this, there are different variables, so, if an option is debatable, try consulting an expert.
2] Disable Fast Startup
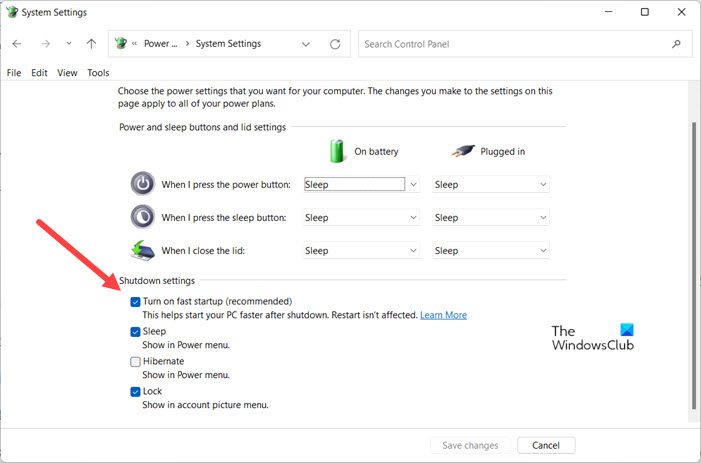
SSDs are known for reducing the time required in the booting process and Fast Startup is meant to do the same. However, Fast Startup on top of SSD’s fast booting speed, doesn’t make a lot of difference. So, it would be better to just disable the Fast Startup and allow your system to boot properly. Follow the given steps to disable Fast Startup.
- Open Control Panel.
- Go to Hardware and Sound > Power Options.
- Click on Change what the power button does > Change settings that are currently available.
- Untick Turn on fast startup.
- Click Save Changes.
This will optimize your SSD.
3] Turn on TRIM
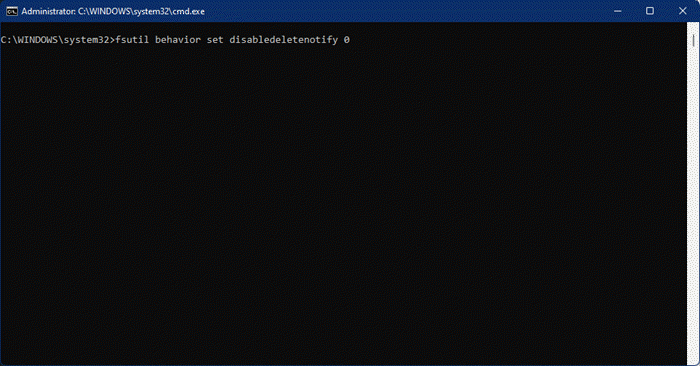
TRIM is a feature that signals the SSD which blocks of data are no longer in use and can be safely wiped out to be writable again. This helps to improve SSD’s performance and should be enabled on your system. Windows tend to keep it enabled by default, but we are still going to check if the feature is working. To do that, open Command Prompt and run the following command.
fsutil behavior set disabledeletenotify 0
If you see Disabled, then TRIM is enabled. I know it’s counterintuitive, but do read the command.
4] Update SSD Firmware and Driver
Next up, try updating SSD Firmware that comes with your drive and try updating your device driver. The firmware can be downloaded from the manufacturer’s website, the device driver can be downloaded from any of the following methods.
This will make sure that you are always up-to-date.
5] Enable AHCI
AHCI is an abbreviation of Advanced Host Controller Interface (AHCI), it specifies the operation of Serial ATA (SATA) host controllers in a non-implementation-specific manner in its motherboard chipsets. You need to enable the AHCI from BIOS and optimize your experience even further.
6] Optimize SSD using Crucial Storage Executive
Crucial Storage Executive is software that will help you in optimizing SSD. It is a firmware that will take care of your Solid State Drive by updating its firmware, driver, and other things. So, go ahead and download Crucial Storage Executive for free.
7] Manage Write Caching
Write Caching is one of the most controversial features. On some systems, it makes the experience better, whereas, on some, it deteriorates the SSD’s performance. What we would suggest is to try to disable Write Caching and if you see a dip in SSD’s performance, turn it back on.
8] Use High Performance Power Plan
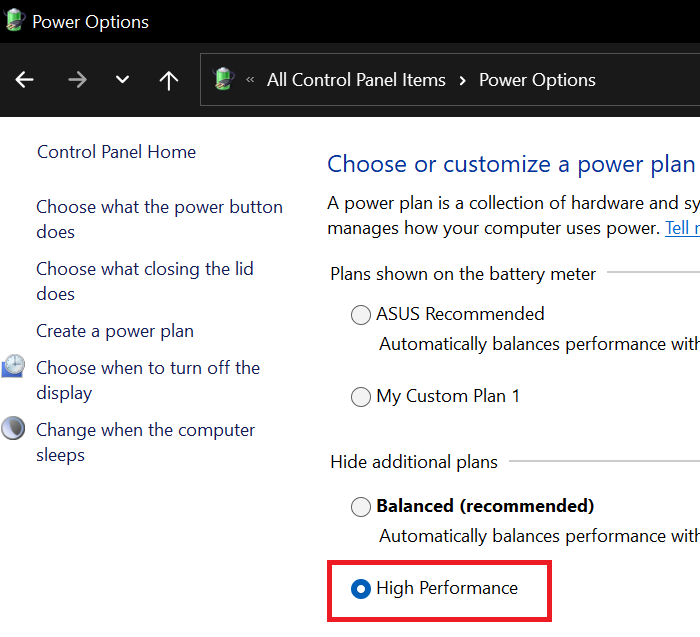
Finally, we would ask you to High Performance Power Plan. This mode works great with SSD, however, it can take a bit of a toll on your battery. So, it’s a bit of a tradeoff, but if you agree, follow the prescribed steps to switch to High Performance Power Plan.
- Open Control Panel.
- Go to Hardware and Sound > Power Options.
- Select High Performance Plan or Ultimate Performance Plan.
Close Control Panel, restart your computer and your SSD will be optimized.
Read: Things you must do when running an SSD in Windows 11.
Is optimization good for SSD?
Yes, optimization is good for everything. However, you need to make sure that you are not over-optimizing things, also, a lot of users tend to do redundant things when trying to optimize their device. So, if you want to optimize your SSD, make sure to just execute the tips mentioned in this guide.
Read: Do you need to defrag SSD?
Does higher SSD increase performance?
Yes, SSDs will increase the performance of your system. They will not only have a faster read and write speed but will only quicken the booting process. So, if you are in a market looking for something to improve your system, SSD should be right on top of your list.
That’s it!
Also Read:Â Fix Slow SSD Read or Write Speed on Windows PC.

VDI-in-a-box, a virtual desktop appliance that runs on commodity server hardware with local storage, allows SMBs to deploy VDI without getting bogged down in the cost and complexity involved with the technology.
Kaviza fills an area of need for Citrix, which hasn't previously addressed the SMB space with a purpose built VDI offering, according to Tom Flink, vice president of worldwide channel and sales strategy at Citrix.
"We think desktop virtualization, and VDI specifically, have a lot of benefits to customers in that space who want to take advantage of the technology but don’t have the resources to deploy it," Flink said in a press conference Monday.
Cupertino, Calif.-based Kaviza is a Citrix partner, and VDI-in-a-box is fully integrated with Citrix's HDX protocol, which optimizes graphics and multimedia performance on virtual desktops and mobile devices.
Kaviza will transition into the Citrix Solution Advisor program on July 1, but VDI-in-a-box is available now from Citrix and channel partners will be able to register Kaviza deals starting June 1, Flink said.
Over the next two quarters, Citrix will work on rebranding Kaviza and working out licensing and partner compensation. In the meantime, select partners will be educated on the technology and how to position it appropriately based on the size and scale of the customer, Flink added.
Kumar Goswami, co-founder and CEO of Kaviza, says VDI-in-a-box has been popular in education and vertical markets where data center virtualization just isn't an option.
"These companies are on a tight budget and have time constraints," Goswami said. "Many of these organizations are limited in terms of infrastructure and they're not looking to get trained."
One of Kaviza's biggest strengths for the channel is its ability to shorten sales cycles, said Kaviza COO Krishna Subramanian. "For some customers, desktop virtualization is still a very new concept. VDI-in-a-box is a way for them to see how the technology works, and the benefits of HDX and a rich user experience," she said.
Kaviza will help extend the work Citrix has been doing with its partner Microsoft in the area of desktop virtualization, Flink said. This work has been focused on the enterprise thus far, but Kaviza will help extend that down into Microsoft's SMS&P partner base, where partners have just begun dipping their toes in the water, he said.
By Jaya Patel, Atul Kumar (eInfochips - An Arrow company)
Abstract:

In a VLSI design, floorplan is the crucial stage in which chip area, size and shape of the chip can be determined. Floorplan is iterative process. When designer is done with the floorplan, the next step is to run placement and optimization, after completion of placement and optimization designer would analyse the congestion map, cell density and timing reports, before moving to next stage i.e. Clock Tree Synthesis. This article discusses about the various approaches to reduce congestion and timing violation by modifying floorplan at block level.
1. Introduction
The design complexity is increasing as the number of transistors on a chip is increasing. So, in the VLSI design flow, Physical design plays a very important role. Floorplanning is the starting step in the physical design flow. The main concern of floorplanning is to find the appropriate location of the module on the layout surface on the basis of interconnectivity. While determining the locations, one important check involved is that there should not be any overlapping between two modules. Designer determines the size of the die at floorplan stage and creates wire tracks for placement of the standard cell. Designer does a power ground connection and determines the I/O pad/pin placement location. The designer should take care of sanity checks at floorplan stage. Main aim of the floorplan is: -
- Minimize the area.
- Minimize the total wire length.
- Improve routability.
- Minimize delay.
- Minimize cost
At placement and optimization stage, PnR Tool tries to optimize data path so that data arrival time can be minimized and worst negative slack (WNS) and total negative slack (TNS) could be reduced. Placement is the process of finding a suitable physical location for each cell in the design. The quality of routing in design is highly determined by the placement. If more number of cells are placed in a small area then the number of routing tracks available for routing is less than the required routing tracks, which may cause congestion in the design. There are several reasons for congestions:
- High standard cell density in a small area.
- Placement of standard cell near macros.
- High pin density at the edge of the macro.
- Bad floorplan.

Figure 1. Congestion near the port
Congestions near the port is shown in figure 1. The designer must take care of these issues at the beginning by applying placement blockages (soft, hard, partial blockage), keep-out margin, Scan chain Re-ordering, cell padding, macro padding and create bounds. Creating bound allows the user to define region-based placement.
2. Design Challenges
In this article, two challenges would be discussed: -
- Congestion near to the feedthrough port, most of the cells placed near the port and forms the crisscross path with another port.
- Another challenge is to Reg2out violation. In this case, 48 flip flop are placed at one location and interacting with all macros placed at left side and the port placed at left top of the design.
Case 1: fixing congestion near feedthrough port
This section describes a port swapping technique by which congestion can be reduced near the ports. While doing swapping of the port, designer has to take care of the other block also. If that port of the block is interacting with other blocks, then swapping of the ports will be done accordingly. In the figure 2, top ports that are pink in color represent feed_input ports and feed_output port on the right bottom side. Similarly, for blue color top right side is feed_output and right one is feed_input port. Instances that are highlighted in blue and pink color are registers.

Figure 2.feed_input and feed_output ports
In figure 3, Top right feed_input ports which are in blue color are interacting with feed_output port which is green in color which is placed on right edge of the block and we see there is one pipe line registers between them which is shown by yellow color line.

Figure 3. Interaction between feed_input and feed_output ports
Implementation:

Figure 4 After swapping feed_input and feed_output ports
As shown in figure 4, right side feed_input* ports are swapped with feed_output* ports to improve congestion by reducing criss-cross near the ports. After implementing this Congestion improved from 4.4% to 2.2%.
Case 2: Fixing Register to output (REG2OUT) setup violation-
At floorplan stage, Macro/IP placement, pin/port placement and power planning are performed. Only setup violations would be reported at placement stage, and hold violations will be reported after CTS stage in Pnr flow.
Path groups would be creating for the timing path. This enables reporting the timing results separately for each group, as well as set the options to focus the timing optimization on specific critical timing path groups.
Command (in Innovus) createBasicPathGroups – expanded can be used to create reg2reg, reg2Cgate, in2reg, reg2out, and in2out path groups.

Figure 5 : Different timing path groups
In the above figure path between flip-flop 1 and flip-flop 2 is called as reg2reg path and the path between flip-flop 2 and the output port is called as reg2out path. The reg2reg and reg2cgate default path groups are high effort path groups for optimization and the remaining path groups are low effort path groups. We can also create custom path groups according to the requirement. STA person would define constraints for I/O timing e.g. input delay, external delay etc. in Synopsys design constraint (SDC) file. Virtual clocks are defined to constraint the I/O timing paths. While doing PnR at block-level, I/O timing should be met even though internal timing has the higher priority. While doing timing optimization, tool will locate flip-flops according to timing requirements. As internal timing has higher priority, it might be possible that the tool would place flip-flops little away from the I/O port.
METHODOLOGY: -
To fix IO timing violation, we need to analyze the cause of the timing violations so that it can be fixed at the right stage. In this design, reg2out setup violation reported at placement stage. To meet the internal timing, tool placed those flops a little away from the output port. These violations need to be addressed at the placement stage itself. It was found that there was enough margin in previous timing paths (reg2reg). So flopbound could be created near the output port to fix the reg2out setup violations. Now there are few things that need to be identify: -
- location of the bound
- Size of the bound
- Which group should be created out of soft Guide, Guide, Region and Fence.
PnR tool, Innovus support four type of physical floorplan constraints namely soft guide, guide, region and fence.
Soft Guide: -
Soft guide constraints are similar to a guide constraint except that there are no fixed locations. The soft guide constraints are not as restrictive as a fence or region constraint, so some instances/cell might be placed further away if there are talking to other modules.
Guide:
It roughly defines an area within which the PnR tool place instances/cells of given module. Instances from modules that are not part of the guide might be placed inside the guide if the area of the guide is underutilized. Similarly, cells from the modules defined as the part of the guide may be placed outside if the area of the guide is over utilized. So basically, a guide is a soft indicant for the placement of the cell that may let some cells in and let some cells out.
Region:
The region constraint is also a loose constraint. However, it is stronger than the guide constraint. When region is created, it requires all the cells of the modules contained in the defined region to be placed in the specific region area. If there is an extra space in the region, other cells from the other modules might be placed inside.
Fence:
The fence constraint is the strongest floorplan constraint. It would not allow cells from other modules to be placed inside even if the area is underutilized. Additionally, the cells in a fenced area cannot be placed outside the defined fence area.
Now it is very important to choose which type of physical floorplan constraints need to be selected for creating the flop bound. Four types of floorplan constraints have been described above.
For this case, a region had been created as the flops would be placed together and at the specified location, moreover, other cells from other modules could also be placed inside region if some extra space would be there, hence the area can be utilized completely. The distance between the output port and the bound depends on the setup slack of violating timing paths and the margin available in the previous paths. Finding the appropriate location of the flip-flop bound is an iterative process.
First, the designer has to select one location based on parameter described earlier and checked the timing violations, if violation had not been reduced to the desired limit, then the flop bound would be shifted nearer to output port and then again check the timing report. If the slack of timing path is under the desired limit, that would be the final location of the flop bound. Cells those need to be pulled inside the bound would be selected before creating the region for the flops. Start by creating an instance group and assigning members to the group. Then region would be created using the group name.
Implementation:
In the design, a region of 48 flops has been created near the output port and it would prevent the spreading of those flops. Hence, reg2out setup violations can be reduced to the desired limit.
Specification of block
|
Dimension |
2126 x 976.68 |
|
Instances |
1.06 M |
|
Utilization |
17% |
|
Macro count |
220 |

Figure6: Interaction of 48flops with highlighted macros at first level
In the figure shown above, output port has been highlighted and placement of the registers has been shown before creating region.

Figure7. bound of 48 flops
In this figure, location of the region has been shown in the design. It makes sure that internal timing should not get violated while fixing reg2out timing violations. Reg2out setup timing violation reduced to desired limit after implementation of above methodology.
CONCLUSION:
Floorplanning is an important and critical step of the PnR flow. If the quality of floorplan is not remarkable, it can create different issues like congestion, timing violations, routing issues and IR drop etc. Few real design scenarios have been discussed here. Placement of feedthrough ports at the appropriate location is required to control the congestion and reduce the cell density at the specified area. For I/O timing violations, identifying real cause is essential to apply the required approach for fixing the violations.
Creating bound could be one approach to address the I/O timing violations at floorplan stage. This would also help in reducing the number of buffers/inverters inserted by the tool for the optimization in I/O timing paths. Size and location of the bound should be selected carefully by the designer. Multiple bounds can be created in the design as per the requirement.
“eInfochips, an Arrow company, is a leading global provider of product engineering and semiconductor design services. With over 500+ products developed and 40M deployments in 140 countries, eInfochips continues to fuel technological innovations in multiple verticals.
For more information connect with eInfochips today.”
REFERENCE
[1] https://support.cadence.com/
[2] A Practical Approach to VLSI System on Chip (SoC) Design. Author: Chakravarthi , Veena
[3] J. Bhasker and R. Chadha, Static timing analysis for nanometer designs: A practical approach. 2009.
ACKNOWLEDGEMENT
The authors would like to thank EInfochips Company for making the required resources accessible.
Authors
|
Jaya Patel
|
|
Atul Kumar
|
If you wish to download a copy of this white paper, click here
Confirming reports that have been circulating for weeks, Citrix Systems is being bought by private equity firms Vista Equity Partners and Evergreen Coast Capital for $104 per share.

Citrix Systems is being acquired and taken private in an all-cash deal valued at $16.5 billion and will be combined with data integration and analysis software developer Tibco Software, the companies said Monday.
Citrix is being bought by Vista Equity Partners and Evergreen Coast Capital, the latter an affiliate of Elliott Investment Management. Tibco has been owned by Vista Equity Partners since 2014.
The announcement confirms reports that have been circulating for weeks that Citrix was in negotiations to be acquired by Vista Equity Partners and Elliott Management.
[Related: Citrix CEO David Henshall Steps Down]
The deal has been unanimously approved by the Citrix board of directors and is expected to close by mid-year, subject to customary closing conditions, Citrix shareholder approval and regulatory approvals. Elliott Management and its affiliates, which own about 12 percent of Citrix shares, will vote their shares in favor of the deal.
Citrix shareholders will receive $104.00 in cash per share under the deal, representing a 30 percent premium over the company’s five-day volume-weighted average price as of Dec. 7, 2021, “the last trading day before market speculation regarding a potential transaction” began, according to a Citrix statement, and a 24 percent premium over the Dec. 20, 2021, closing price, the last trading day prior to media reports about a potential bid from Vista Equity Partners and Evergreen Coast Capital.
Citrix’s stock closed at $105.55 per share on Friday, Jan. 28, but opened at $101.79 Monday morning, down nearly 4 percent.
Once the acquisition is complete, Citrix will become a private company, will continue to operate under the Citrix name and brand, and will remain based in Fort Lauderdale, Fla.
Jed Ayres, CEO of secure edge operating system powerhouse IGEL, which works closely with Citrix in the VDI market, said he sees the deal as a game-changer that brings together two storied technology companies to create a “cohesive platform that delivers on connected data and apps with the security” that is demanded in a hybrid cloud marketplace.
“If Citrix and Tibco can deliver on this vision, they will do very well,” he said. “Both of these companies have a storied history. These are two companies that are in every large enterprise customer in the world. They have an opportunity now as a private company to build a very cohesive platform that connects people to data and applications with the right analytics and security. The big question is how well and how quickly they can integrate their offerings. Regardless, going private will help Citrix continue their transition to the cloud without the pressure of being a publicly held company.”
Citrix is a provider of secure digital workspace and application delivery software. Tibco, based in Palo Alto, Calif., markets data management, integration and analysis software, much of it acquired through a series of acquisitions over more than 20 years.
The Citrix acquisition and combination with Tibco will “accelerate Citrix’s defined growth strategy and Saas transition,” the companies said.
The Citrix-Tibco merger “will create one of the world’s largest software providers, serving 400,000 customers, including 98 percent of the Fortune 500 with 100 million users in 100 countries,” the companies said in a statement.
The combined company “will be positioned to provide complete, secure and optimized infrastructure for enterprise application and desktop delivery and data management to advance hybrid cloud IT strategies and meet the needs of the modern enterprise,” the statement said.
“Today’s announcement is the culmination of a strategic review process conducted over five months, including extensive outreach to both potential financial and strategic buyers. This transaction provides our shareholders with significant immediate cash value. Moreover, this investment by Vista and Evergreen is a testament to the value Citrix has created and the reputation our team has built,” said Bob Calderoni, chairman of the Citrix board of directors and interim president and CEO, in a statement.
“Over the past three decades, Citrix has established itself as the clear leader in secure hybrid work. Our market-leading platform provides secure and reliable access to all of the applications and information employees need to get work done, wherever it needs to get done,” Calderoni continued.
“By combining with Tibco, we will expand this platform and the outcomes our customers achieve. Together with Tibco, we will be able to operate with greater scale and provide a larger customer base with a broader range of solutions to accelerate their digital transformations and enable them to deliver the future of hybrid work. As a private company, we will have increased financial and strategic flexibility to invest in high-growth opportunities, such as DaaS [Data as a Service], and accelerate its ongoing cloud transition,” Calderoni said.
“There has never been a better time to be in the business of connected intelligent analytics, and we’re thrilled to bring our industry-leading solutions to Citrix’s global customers,” said Tibco CEO Dan Streetman in the statement. “The workplace has changed forever, and companies everywhere will require real-time access to faster, smarter insights from the increasingly large volumes of data available to them, their employees, and their ecosystems. I couldn’t be more excited about our combined vision and look forward to a strong partnership.”
A Tibco spokesperson said the companies are not disclosing additional details about the deal or making company executives available for comment.
1Y0-341 thinking | 1Y0-341 test prep | 1Y0-341 approach | 1Y0-341 test | 1Y0-341 study help | 1Y0-341 testing | 1Y0-341 Free PDF | 1Y0-341 download | 1Y0-341 resources | 1Y0-341 health |
Killexams Exam Simulator
Killexams Questions and Answers
Killexams Exams List
Search Exams